GitLab offers integration with Google Kubernetes Cluster and Amazon Elastic Kubernetes Services. To follow this article, you need a Google Kubernetes Cluster and GitLab account. I am sure you can obtain a GitLab account if you haven’t got one, and I have you covered with creating a GKE cluster in this article: Deploy WebApp using Google Kubernetes Engine.
So let’s get started.
Step 1: Add GKE cluster
In GitLab, go to side panel > Operations > Kubernetes > Integrate with a cluster certificate
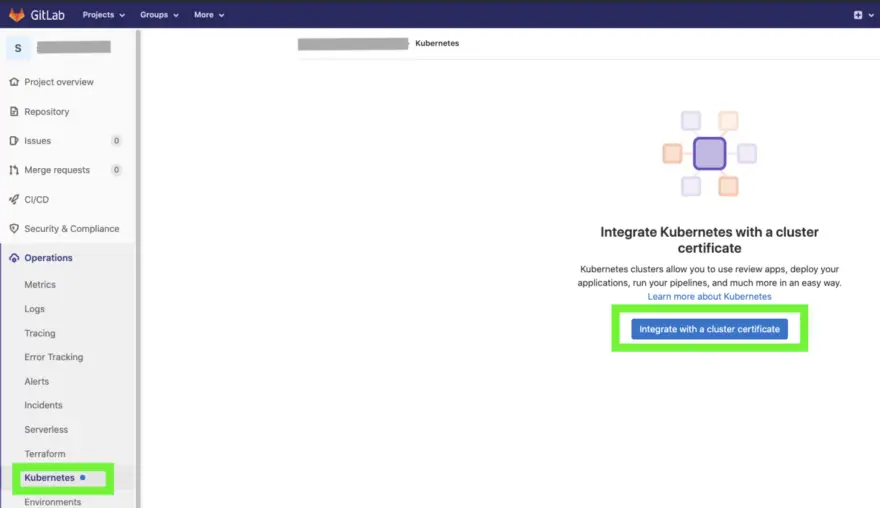
Select Connect existing cluster > Google GKE

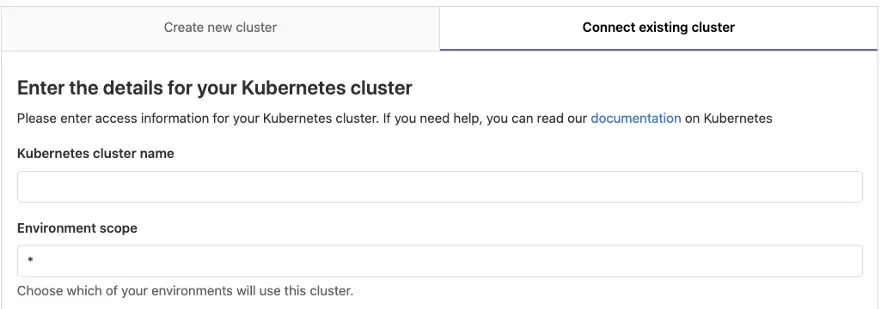
Step 2: Add Cluster information
Cluster name is an identifier for GitLab, so the name can be different from the GKE Cluster name. Leave environment scope with the wildcard, unless you wish to specify it, such as production or staging.
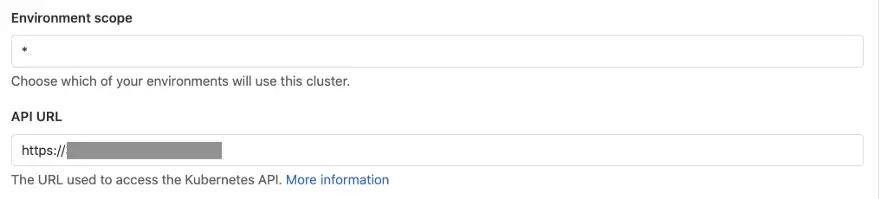
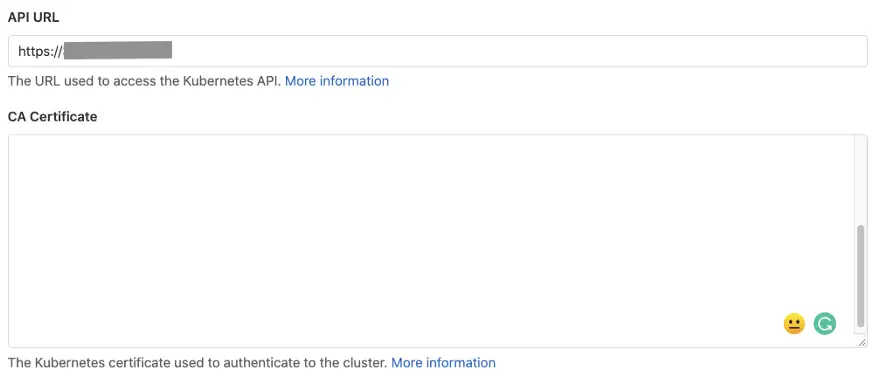
Step 3: Add API URL and Certificate
You can either perform this action from cloud CLI if you have the Cloud SDK installed, or go to your GKE cloud shell from your project. Get the API URL by running the following command:
kubectl cluster-info | grep -E 'Kubernetes master|Kubernetes control plane' | awk '/http/ {print $NF}'
In return, you will receive a base URL, either as a domain name: www.example.com or with IP address, add this API URL to your GitLab console.
Step 4: Add Kubernetes CA Certificate
First of all, list the secrets with command and copy the token which looks like default-token-abcdef:
kubectl get secrets
Second, obtain the certificate with the following command:
kubectl get secret <secret name> -o jsonpath="{['data']['ca\.crt']}" | base64 --decodeCopy the certificate into your GitLab console, and bonus point by highlight the certificate from the command line, it automatically copies the content for you, please don’t select copy because it might also add line-break.
Step 5: Add Kubernetes CA Certificate
From your terminal, create a file called gitlab-admin-service-account.yaml
vi gitlab-admin-service-account.yamlCopy following content into the file:
apiVersion: v1
kind: ServiceAccount
metadata:
name: gitlab
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: gitlab-admin
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: gitlab
namespace: kube-system
Save and quit the vi editor with the below command and click enter:
:wq
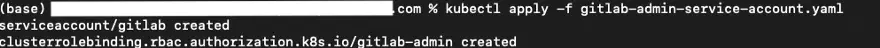
Apply the service account to your cluster:
kubectl apply -f gitlab-admin-service-account.yaml
You should see content from the terminal:
Obtain the token:
kubectl -n kube-system describe secret $(kubectl -n kube-system get secret | grep gitlab | awk '{print $1}')
Copy the token value to GitLab console:
Data
====
token: <authentication_token>
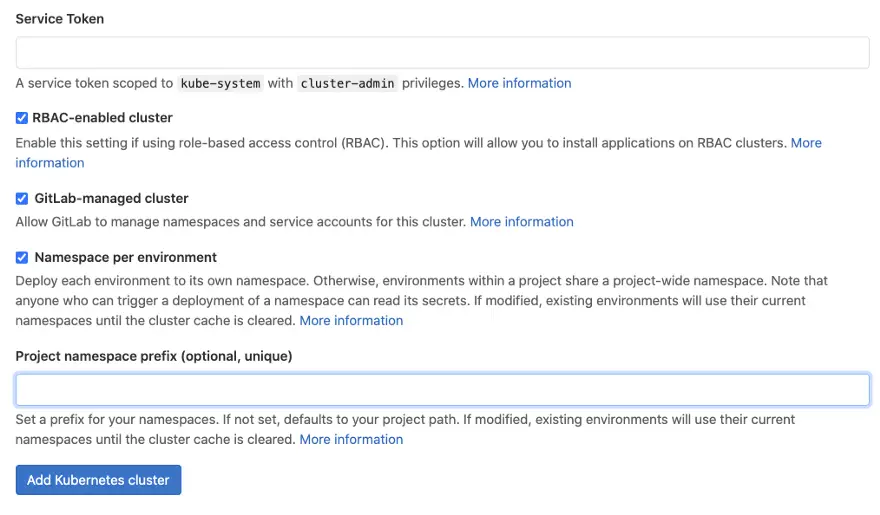
Add a project namespace prefix if you prefer a String name rather than random numbers. Click the blue-button and job done! ✅